RouterOS Socksify连接多节点与加密隧道传输
考虑到有多个SOCKS代理服务节点,如何通过Socksify去同时连接不同的节点,并将内网不同主机重定向到指定的SOCKS代理,由于Socksify不涉及三层路由配置,只涉及dstnat操作所以。一些大型企业多地有服务,服务之间的内部Web服务考虑数据安装,需要使用加密隧道,还会涉及到隧道的搭建。
首先通过3个SOCKS代理节点作为示例,不考虑加密隧道,如下图:
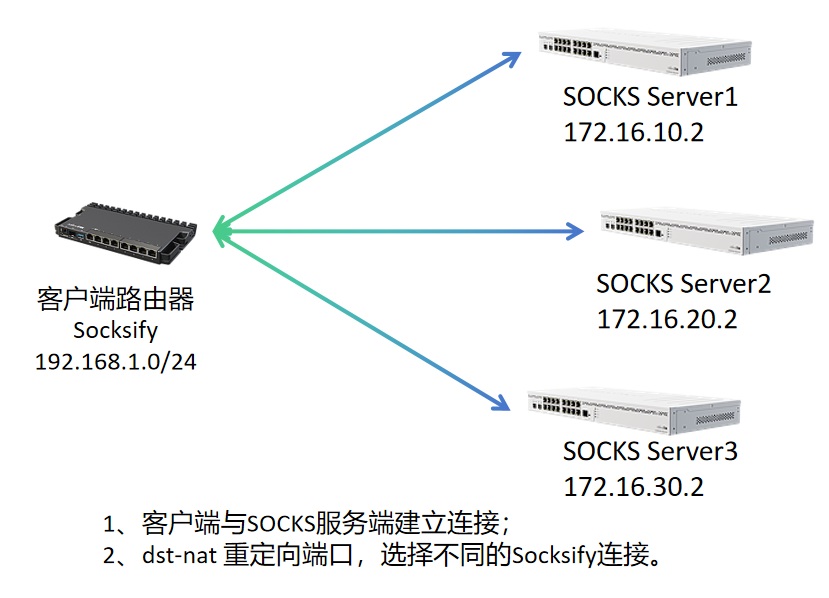
如上图,有3个代理节点SOCKS Server1,SOCKS Server2和SOCKS Server3部署到公网网络都有可以直接访问的公网IP,客户端路由通过Socksify同时连接3个节点,将192.168.1.0/24内的主机根据需要分配到不同的3个节点。每个代理节点使用SOCKS v5协议,端口为TCP 1122,启用账号认证功能。
以下配置通过命令行操作
一、直连SOCKS示例
1.1 SOCKS Server1代理配置
基本IP地址配置
[admin@SOCKS1] >/ip/address [admin@SOCKS1] /ip/address>add address=172.16.10.2/24 interface=ether1
默认路由配置
[admin@SOCKS1] /ip/address>/ip/route [admin@SOCKS1] /ip/route>add gateway=172.16.10.1
路由器DNS配置
[admin@SOCKS1] /ip/route>/ip/dns [admin@SOCKS1] /ip/dns>set servers=223.5.5.5
srcnat配置
[admin@SOCKS1] /ip/dns>/ip firewall nat [admin@SOCKS1] /ip/firewall/nat>add chain=srcnat out-interface=ether1 action=masquerade
创建SOCKS V5代理服务和连接的账号密码
[admin@SOCKS1] >/ip/socks [admin@SOCKS1] /ip/socks> set port=1122 version=5 authentication-method=password [admin@SOCKS1] /ip/socks>users [admin@SOCKS1] /ip/socks/users> add name=user1 password=123
1.2 SOCKS Server2代理配置
基本IP地址配置
[admin@SOCKS2] >/ip/address [admin@SOCKS2] /ip/address>add address=172.16.20.2/24 interface=ether1
默认路由配置
[admin@SOCKS2] /ip/address>/ip/route [admin@SOCKS2] /ip/route>add gateway=172.16.20.1
路由器DNS配置
[admin@SOCKS2] /ip/route>/ip/dns [admin@SOCKS2] /ip/dns>set servers=223.5.5.5
srcnat配置
[admin@SOCKS2] /ip/dns>/ip firewall nat [admin@SOCKS2] /ip/firewall/nat>add chain=srcnat out-interface=ether1 action=masquerade
创建SOCKS V5代理服务和连接的账号密码
[admin@SOCKS2] >/ip/socks [admin@SOCKS2] /ip/socks> set port=1122 version=5 authentication-method=password [admin@SOCKS2] /ip/socks>users [admin@SOCKS2] /ip/socks/users> add name=user1 password=123
1.3 SOCKS Server3代理配置
基本IP地址配置
[admin@SOCKS3] >/ip/address [admin@SOCKS3] /ip/address>add address=172.16.30.2/24 interface=ether1
默认路由配置
[admin@SOCKS3] /ip/address>/ip/route [admin@SOCKS3] /ip/route>add gateway=172.16.30.1
路由器DNS配置
[admin@SOCKS3] /ip/route>/ip/dns [admin@SOCKS3] /ip/dns>set servers=223.5.5.5
srcnat配置
[admin@SOCKS3] /ip/dns>/ip firewall nat [admin@SOCKS3] /ip/firewall/nat>add chain=srcnat out-interface=ether1 action=masquerade
创建SOCKS V5代理服务和连接的账号密码
[admin@SOCKS3] >/ip/socks [admin@SOCKS3] /ip/socks> set port=1122 version=5 authentication-method=password [admin@SOCKS3] /ip/socks>users [admin@SOCKS3] /ip/socks/users> add name=user1 password=123
1.4 Socksify客户端配置
客户端的RouterOS是一个单线接入,并已经完成基本的网络配置
Socksify配置
[admin@client] >/ip/socksify [admin@client] /ip/socksify>add disabled=no name=socks1 socks5-password=123 socks5-port=1122 socks5-server=172.16.10.2 socks5-user=user1 [admin@client] /ip/socksify>add disabled=no name=socks2 socks5-password=123 socks5-port=1122 socks5-server=172.16.20.2 socks5-user=user1 [admin@client] /ip/socksify>add disabled=no name=socks3 socks5-password=123 socks5-port=1122 socks5-server=172.16.30.2 socks5-user=user1
默认srcnat的masquerade规则已经配置,下面是dstnat,让192.168.1.10走socks1,192.168.1.20走socks2,192.168.1.30走socks3
[admin@client] /ip/socksify>/ip firewall nat [admin@client] /ip/firewall/nat>add action=socksify chain=dstnat dst-port=80,443 protocol=tcp socksify-service=socks1 src-address=192.168.1.10 [admin@client] /ip/firewall/nat>add action=socksify chain=dstnat dst-port=80,443 protocol=tcp socksify-service=socks2 src-address=192.168.1.20 [admin@client] /ip/firewall/nat>add action=socksify chain=dstnat dst-port=80,443 protocol=tcp socksify-service=socks3 src-address=192.168.1.30
以上的方式是客户端直接连接SOCKS服务端,数据通过明文传输为经过加密,存在安全隐患。
二、基于加密隧道的SOCKS传输
为保证企业数据的安全传输,可以选择多种隧道方式,例如IPSec、IPSec+L2TP、OpenVPN、SSTP和IPIP+IPSec,以及Wireguard等,使SOCKS连接从隧道通信。下面示例选择Wireguard方式,需要SOCKS的服务端具备公网IP访问,让客户端与服务端建立Wireguard的点对点连接。
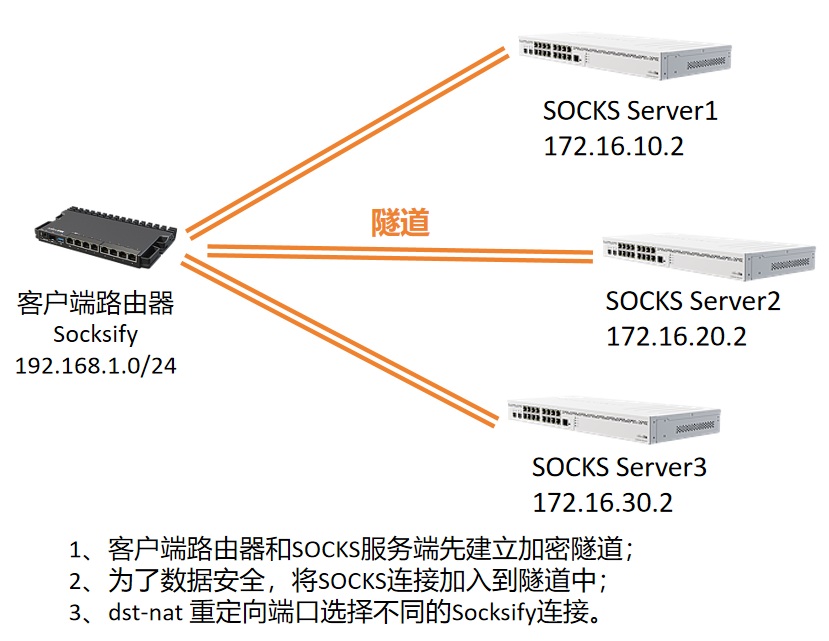
Wireguard连接是通过UDP协议建立,而SOCKS是基于TCP的端口代理,也就是将SOCKS的TCP包封装到Wireguard的UDP隧道中传输。以下示例通用使用命令行配置
2.1 客户端配置Wireguard配置
Socksify客户端需要创建三个Wireguard接口,分别取名socks1,socks2和socks3
[admin@client] >/interface wireguard [admin@client] /interface/wireguard>add listen-port=53869 mtu=1420 name=socks1 [admin@client] /interface/wireguard>add listen-port=53869 mtu=1420 name=socks2 [admin@client] /interface/wireguard>add listen-port=53869 mtu=1420 name=socks2
使用print命令查看,记住public-key后面连接需要使用
[admin@client] /interface/wireguard> print Flags: X - disabled; R - running 0 R name="socks1" mtu=1420 listen-port=53869 private-key="4I8I8eMnd5UZoOXjtD9NPP3k=" public-key="client-key1=" 1 R name="sock2" mtu=1420 listen-port=53869 private-key="SJ4UWerXFGlsnxUbDPJhFXQ=" public-key="client-key2=" 2 R name="sock3" mtu=1420 listen-port=53869 private-key="ukn4UWerTxlsnxUbDPJ3121=" public-key="client-key3="
为每个wireguard接口配置IP地址,
- socks1连接使用10.0.1.0/24段,客户端配置10.0.1.2,服务端配置10.0.1.1
- socks2连接使用10.0.2.0/24段,客户端配置10.0.2.2,服务端配置10.0.2.1
- socks3连接使用10.0.3.0/24段,客户端配置10.0.3.2,服务端配置10.0.3.1
客户端IP配置:
[admin@client] /interface/wireguard>/ip address [admin@client] /ip/address>add address=10.0.1.2/24 interface=socks1 [admin@client] /ip/address>add address=10.0.2.2/24 interface=socks2 [admin@client] /ip/address>add address=10.0.2.2/24 interface=socks3
2.2 SOCKS Server1配置
配置用于连接的出口IP,路由和DNS,以及srcnat规则
[admin@SOCKS1] /ip/address>add address=172.16.10.2/24 interface=ether1 [admin@SOCKS1] /ip/address>/ip route [admin@SOCKS1] /ip/route>add gateway=172.16.10.1 [admin@SOCKS1] /ip/dns>set servers=223.5.5.5 [admin@SOCKS1] /ip/dns>/ip firewall nat [admin@SOCKS1] /ip/firewall/nat>add chain=srcnat out-interface=ether1 action=masquerade
创建Wireguard接口,取名clent1,端口使用53869
[admin@SOCKS1] >/interface wireguard [admin@SOCKS1] /interface/wireguard>add listen-port=53869 mtu=1420 name=client1
使用print命令,记录下public-key
[admin@SOCKS1] /interface/wireguard> print Flags: X - disabled; R - running 0 R name="client1" mtu=1420 listen-port=53869 private-key="4I8I8e94nHY3VkqwbjtD9NPP3k=" public-key="socks1-key="
配置peers参数,用于匹配客户端的socks1的Wireguard请求,允许10.0.1.0/24通过,在public-key填写之前客户端Wireguard的client-key1
[admin@SOCKS1] /interface/wireguard>peers [admin@SOCKS1] /interface/wireguard/peers>add allowed-address=10.0.1.0/24 interface=client1 name=peer1 persistent-keepalive=10s public-key="client-key1="
配置SOCKS1的Wireguard IP地址
[admin@SOCKS1] /interface/wireguard/peers>/ip address [admin@SOCKS1] /ip/address>add address=10.0.1.1/24 interface=client1
配置SOCKS服务和认证账号密码
[admin@SOCKS1] /ip/address>/ip/socks [admin@SOCKS1] /ip/socks> set port=1122 version=5 authentication-method=password [admin@SOCKS1] /ip/socks>users [admin@SOCKS1] /ip/socks/users> add name=user1 password=123
2.3 SOCKS Server2配置
配置用于连接的出口IP,路由和DNS,以及srcnat规则
[admin@SOCKS2] /ip/address>add address=172.16.20.2/24 interface=ether1 [admin@SOCKS2] /ip/address>/ip route [admin@SOCKS2] /ip/route>add gateway=172.16.20.1 [admin@SOCKS2] /ip/dns>set servers=223.5.5.5 [admin@SOCKS2] /ip/dns>/ip firewall nat [admin@SOCKS2] /ip/firewall/nat>add chain=srcnat out-interface=ether1 action=masquerade
创建Wireguard接口,取名clent2,端口使用53869
[admin@SOCKS2] >/interface wireguard [admin@SOCKS2] /interface/wireguard>add listen-port=53869 mtu=1420 name=client2
使用print命令,记录下public-key
[admin@SOCKS2] /interface/wireguard> print Flags: X - disabled; R - running 0 R name="client2" mtu=1420 listen-port=53869 private-key="4I8I8e94nHY3VkqwbjtD9NPP3k=" public-key="socks2-key="
配置peers参数,用于匹配客户端的socks2的Wireguard请求,允许10.0.2.0/24通过,在public-key填写之前客户端Wireguard的client-key2
[admin@SOCKS2] /interface/wireguard>peers [admin@SOCKS2] /interface/wireguard/peers>add allowed-address=10.0.2.0/24 interface=client2 name=peer1 persistent-keepalive=10s public-key="client-key2="
配置SOCKS2的Wireguard IP地址
[admin@SOCKS2] /interface/wireguard/peers>/ip address [admin@SOCKS2] /ip/address>add address=10.0.2.1/24 interface=client2
配置SOCKS服务和认证账号密码
[admin@SOCKS2] /ip/address>/ip/socks [admin@SOCKS2] /ip/socks> set port=1122 version=5 authentication-method=password [admin@SOCKS2] /ip/socks>users [admin@SOCKS2] /ip/socks/users>add name=user1 password=123
2.4 SOCKS Server3配置
配置用于连接的出口IP,路由和DNS,以及srcnat规则
[admin@SOCKS3] /ip/address>add address=172.16.20.2/24 interface=ether1 [admin@SOCKS3] /ip/address>/ip route [admin@SOCKS3] /ip/route>add gateway=172.16.20.1 [admin@SOCKS3] /ip/dns>set servers=223.5.5.5 [admin@SOCKS3] /ip/dns>/ip firewall nat [admin@SOCKS3] /ip/firewall/nat>add chain=srcnat out-interface=ether1 action=masquerade
创建Wireguard接口,取名clent3,端口使用53869
[admin@SOCKS3] >/interface wireguard [admin@SOCKS3] /interface/wireguard>add listen-port=53869 mtu=1420 name=client3
使用print命令,记录下public-key
[admin@SOCKS3] /interface/wireguard> print Flags: X - disabled; R - running 0 R name="client3" mtu=1420 listen-port=53869 private-key="4I8I8e94nHY3VkqwbjtD9NPP3k=" public-key="socks3-key="
配置peers参数,用于匹配客户端的socks3的Wireguard请求,允许10.0.3.0/24通过,在public-key填写之前客户端Wireguard的client-key3
[admin@SOCKS3] /interface/wireguard>peers [admin@SOCKS3] /interface/wireguard/peers>add allowed-address=10.0.3.0/24 interface=client3 name=peer1 persistent-keepalive=10s public-key="client-key3="
配置SOCKS2的Wireguard IP地址
[admin@SOCKS3] /interface/wireguard/peers>/ip address [admin@SOCKS3] /ip/address>add address=10.0.3.1/24 interface=client1
配置SOCKS服务和认证账号密码
[admin@SOCKS3] /ip/address>/ip/socks [admin@SOCKS3] /ip/socks> set port=1122 version=5 authentication-method=password [admin@SOCKS3] /ip/socks>users [admin@SOCKS3] /ip/socks/users> add name=user1 password=123
2.5 回到client配置
配置客户端的Wireguard peers,需要创建3条peer对应3个节点SOCKS,并导入对应节点的public-key,
- SOCKS服务器1的endpoint-address=172.16.1.2 endpoint-port=53869
- SOCKS服务器2的endpoint-address=172.16.2.2 endpoint-port=53869
- SOCKS服务器2的endpoint-address=172.16.3.2 endpoint-port=53869
具体配置如下:
[admin@client] /interface/wireguard>peers [admin@client] /interface/wireguard/peers>add allowed-address=10.0.1.0/24 endpoint-address=172.16.1.2 endpoint-port=53869 interface=socks1 name=peer1 persistent-keepalive=10s public-key="socks1-key=" [admin@client] /interface/wireguard/peers>add allowed-address=10.0.2.0/24 endpoint-address=172.16.2.2 endpoint-port=53869 interface=socks2 name=peer2 persistent-keepalive=10s public-key="socks2-key=" [admin@client] /interface/wireguard/peers>add allowed-address=10.0.3.0/24 endpoint-address=172.16.3.2 endpoint-port=53869 interface=socks3 name=peer3 persistent-keepalive=10s public-key="socks3-key="
这样完成服务端到客户端的Wireguard连接,现在需要配置socksify
[admin@client] >/ip/socksify [admin@client] /ip/socksify>add disabled=no name=socks1 socks5-password=123 socks5-port=1122 socks5-server=10.0.1.1 socks5-user=user1 [admin@client] /ip/socksify>add disabled=no name=socks2 socks5-password=123 socks5-port=1122 socks5-server=10.0.2.1 socks5-user=user1 [admin@client] /ip/socksify>add disabled=no name=socks3 socks5-password=123 socks5-port=1122 socks5-server=10.0.3.1 socks5-user=user1
默认srcnat的masquerade规则已经配置,下面是dstnat,让192.168.1.10走socks1,192.168.1.20走socks2,192.168.1.30走socks3
[admin@client] /ip/socksify>/ip firewall nat [admin@client] /ip/firewall/nat>add action=socksify chain=dstnat dst-port=80,443 protocol=tcp socksify-service=socks1 src-address=192.168.1.10 [admin@client] /ip/firewall/nat>add action=socksify chain=dstnat dst-port=80,443 protocol=tcp socksify-service=socks2 src-address=192.168.1.20 [admin@client] /ip/firewall/nat>add action=socksify chain=dstnat dst-port=80,443 protocol=tcp socksify-service=socks3 src-address=192.168.1.30
需注意客户端的DNS解析配置,根据不同场景进行调试



